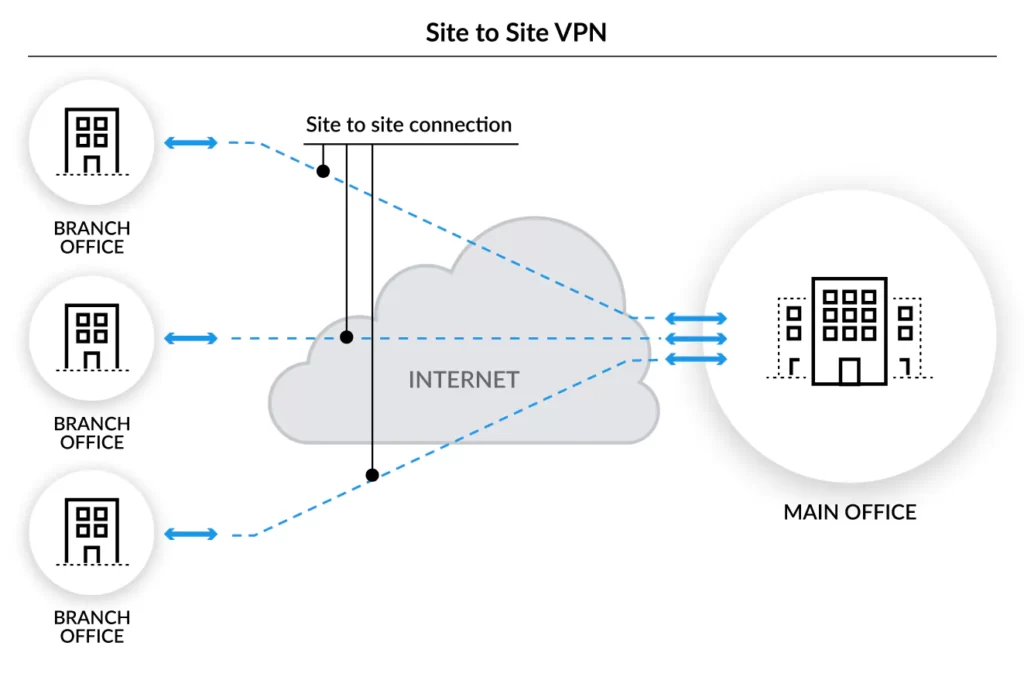
A site-to-site virtual private network (VPN) is a link established between two or more networks. This could be a corporate network in which numerous offices collaborate or a branch office network with a central office and multiple branch locations.
Creating an Internet-based Site-to-Site VPN
Site-to-site VPNs are useful for businesses that prioritize private, secure traffic, and they are especially valuable for businesses with several offices spread across wide geographical areas. These businesses frequently require access to resources stored on a primary network, such as servers that facilitate email or store data. In some cases, a server may function as the operational hub for an application critical to the company’s operations.
A site-to-site relationship In that instance, VPN can provide complete access to the program to all sites, as if it were situated within their physical facility.
In many ways, the history of site-to-site VPNs connects with the history of the internet itself. Site-to-site VPNs were a precursor to what we now call the internet. They were made feasible by the deployment of the original packet-switching network known as the Advanced Research Projects Agency Network (ARPANET), as well as the early implementations of Transmission Control Protocol/Internet Protocol (TCP/IP).
TCP/IP describes how data is structured into packets, assigned addresses, and transferred and received across multiple computers on the internet. Before the internet, as we know it today, computers were linked between sites via a private network and
TCP/IP. Site-to-site networks predated the internet in this fashion, laying the groundwork for what we have today.
People wanted to disguise their IP addresses and surf the internet more safely, hence the modern incarnation of a VPN grew in popularity. A disguised IP address allows you to download torrents without disclosing your identity. You can also access geo-blocked content regardless of where you are. Furthermore, a public network is subject to a constant bombardment of cyberattacks, whereas a VPN provides a more secure, encrypted connection. Individual consumers preferred private VPNs because of these benefits.
VPNs built for one or a few users at a time, on the other hand, lack the capabilities to meet the needs of a large enterprise. In many circumstances, large corporations must transport many terabytes of data between locations fast and reliably, and a VPN adequate for a typical torrent user or web surfer would be incapable of handling the task.
How to Create a Site-to-Site VPN
Creating a site-to-site VPN entails deciding how you want data to be moved from one site to the next and select a method to keep it secure from outsiders. This can be accomplished using an internet-based site-to-site VPN or an MPLS-based site-to-site VPN.
Putting Together an Internet-Based Site-to-Site VPN
An internet-based site-to-site VPN combines an organization’s existing network with the public internet. A VPN gateway that secures data moving back and forth is required to set up an internet-based site-to-site VPN.
To develop an internet-based site-to-site VPN, you build a tunnel between two networks, which requires three components:
A single-site base network
In another area, a satellite network
A tunnel with security gateways on each end
The tunnel either “burrows through” or sits on top of an existing internet connection. However, the tunnel prevents individuals from accessing the traffic passing over it via the physical network. To get started, you’ll need to install a gateway at each location. The data will be encrypted at the first gateway it encounters when it enters the tunnel. Each data packet is encrypted to protect it from users, devices, and viruses that may attempt to damage, steal, or compromise it in some way.
When the data gets to its destination, it comes into contact with the other gateway. This decrypts the data so that it may be read by the network on the other side. Entities in the physical internet that the data must traverse while encrypted will be unable to read it. Without a second gateway to decrypt the data for the receiving network, the data will stay unintelligible.
The gateway may include a network access server and a secure access service edge (SASE), which requires users to submit credentials before connecting to the VPN.
A firewall, which provides a robust barrier between the organization’s private network and the surrounding internet, can also be used. Firewalls can limit the type of traffic that can pass through them.
Why Implement a Site-to-Site VPN
When deciding whether to adopt site-to-site VPN services, there are various variables to consider. In some circumstances, standard IPsec is enough to communicate between two or more locations. However, there are a few factors that may persuade a business to employ VPN connections instead:
- The variety of locales
- Size of a business
- The separation between each site
- The resources that the sites can share with one another
A site-to-site VPN is usually a viable choice if your company has multiple sites with employees that need to share resources offered by the main office. In this circumstance, a site-to-site VPN may ensure that all employees have secure access to the same resources.
Assume you have a corporation headquartered in New York that has many branch offices, one in Shanghai, one in France, and one in Switzerland. Each location employs between 15 and 20 people. A central server houses the company’s email system. You also have a data server that houses critical marketing collateral and proprietary data.
When you utilize a site-to-site VPN, not only can all employees access the same services, but the data is also encrypted, keeping it safe from potential attackers.
5 Key Components of a Site-to-Site VPN
Watertight Protection
Your company’s VPN must be safeguarded by strict security procedures. The data that travels back and forth must be secure, both in transit and while at rest at each site. This necessitates appropriate authorization, authentication, and administration. It is also critical that these procedures support the organization’s security policies, including any established best practices generated by the various IT professionals in each location.
A VPN with properly programmed gateways will only allow data through if it is authenticated. Otherwise, data is discarded, which helps to keep the network safe in many circumstances.
Operational Ease
A VPN that is difficult to use may cause more annoyance than a convenience. Users should be able to connect to the VPN via a web browser. While ease of access is crucial, it should not lead to sloppy security standards. If customers must go through an extra process to access the VPN, the added protection may be worth the few extra moments.
This does not imply that access must be difficult. Employees should be able to connect to the VPN using mobile devices like laptops, tablets, or smartphones in the vast majority of circumstances.
You can also make network administration easier using a VPN. Remote locations can be managed from a central office, and you have complete control over the entire network. This allows you to enhance your security measures, such as installing new features or updating existing software, all from a single spot.
Simple and Secure Scalability
A VPN is simple to scale. In minutes, you may add a new site, user, office, or partner organization. It is simple and inexpensive to add new connections if you do not need to install additional VPN clients at each new location. It is also simple to set up another site if you need to transfer a satellite office.
Business Continuity
In the event of a disaster, whether natural or man-made, it is critical to minimize company interruption and get back up and running as soon as possible. A site-to-site VPN enables you to use remote access as soon as an emergency is discovered.
If a disaster strikes an office, for example, staff are not required to halt all output until everything is back up and running. They can each be given access to the site-to-site VPN, which allows them to connect to resources at headquarters and work from home. With a VPN, you can reduce downtime and the financial impact of a disaster.
Flexible Deployment
A VPN gives you the ability to install a new solution over a large network of devices in diverse physical locations. You can specify which sites will receive the updated solution first, second, and so on. This may allow you to offer training or support in manageable stages rather than addressing it all at once and potentially overwhelming your IT personnel.
