To protect your online data seems not so easy in the current time, especially when attackers are frequently bringing new techniques to steal your online information. Have you ever thought about that someone could sniff your communication without your awareness? Most of the user’s answer will be “NO”. However, this could happen to you, if you are not aware of one of the hazardous cyber attacks named “Man-in-the-middle (MITM) Attack”.
What Is a Man-in-the-Middle Attack?
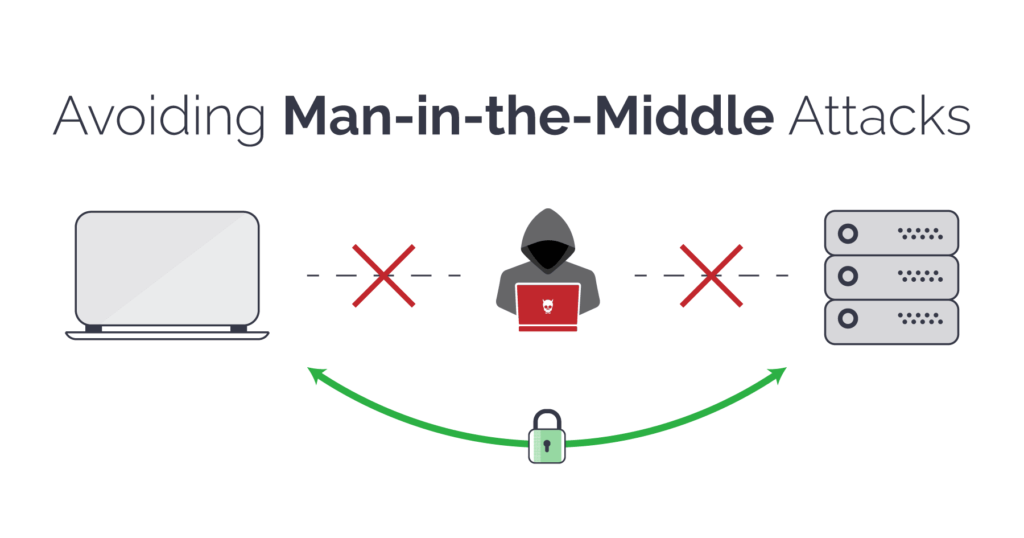
A man-in-the-middle attack is a type of eavesdropping attack, where attackers interrupt an existing conversation or data transfer. After inserting themselves in the “middle” of the transfer, the attackers pretend to be both legitimate participants. This enables an attacker to intercept information and data from either party while also sending malicious links or other information to both legitimate participants in a way that might not be detected until it is too late.
You can think of this type of attack as similar to the game of telephone where one person’s words are carried along from participant to participant until it has changed by the time it reaches the final person. In a man-in-the-middle attack, the middle participant manipulates the conversation unknown to either of the two legitimate participants, acting to retrieve confidential information and otherwise cause damage.
Common abbreviations for a man-in-the-middle attack including MITM, MitM, MiM, and MIM.

Key Concepts of a Man-in-the-Middle Attack
Man-in-the-middle attacks:
- Are a type of session hijacking
- Involve attackers inserting themselves as relays or proxies in an ongoing, legitimate conversation or data transfer
- Exploit the real-time nature of conversations and data transfers to go undetected
- Allow attackers to intercept confidential data
- Allow attackers to insert malicious data and links in a way indistinguishable from legitimate data
Example of MITM:
For example, there are three persons named Robert, Johnny and Tom (attacker). Robert wants to communicate with Johnny. Now, Tom with a view to sniff the communication carries out fake conversion with Johnny behalf of Robert. First, Robert asks Johnny for a public key and when Johnny provides the key to Robert, Tom will intercept the key. Then, Tom will send a fake message to Robert with his own public-key pretending to be a legitimate message coming from Johnny. Robert believes that the communication is legitimate, but it is not true. Finally, Robert encrypts his message with Tom’s public key and sends the converted message back to Johnny.
Before two months, Facebook had a serious security flaw that could invite attacker to sniff a user’s traffic, including access token found by the penetration tester Ahmed Elsobky. Attacker steals Facebook user’s access token that stores information about permission as well tokens itself. After that, an attacker can sniff victim’s data and do any activity on behalf of the user.
Precautions against MITM:
- Always use public-key infrastructure with mutual authentication that will not only protect the application from data sniffing, but also validates the application as a legitimate one.
- Use strong encryption between the client and the server. The server with digital certificate can establish its valid identity that will help both the client and the server to communicate in a secure environment.
- Use time testing techniques that measure the total time of a message delivery time. If it takes more than 60 seconds, then there might be going on an MITM activity.
- Check the credentials on a regular basis. Secure your passwords and make it complex. Keep your password updated every three months.
- Avoid use of public Wi-Fi at a coffee shop, airport or any public place as it might you fall into victim and steal your login credentials.
Role of SSL in prevention of MITM attack:
Insecure information transmission between the server and browser poses a serious risk and can be intercepted by third parties. SSL is the only solution that encrypts the information to prevent it from spying eyes. If we talk about MITM attack there is high chance data sniffing, in that case SSL binds the information with strong 256-bit encryption to keep MITM attack away.