Internet Key Exchange (IKE) plays a crucial role in securing Virtual Private Networks (VPNs) and IPsec protocols. By automating the process of establishing security associations (SAs) between devices, IKE facilitates secure communication over potentially unsafe networks.
Internet Key Exchange (IKE) is a standard protocol that allows two parties to establish a secure and authenticated communication channel across a virtual private network (VPN). The protocol secures VPN negotiation, remote host access, and network access.
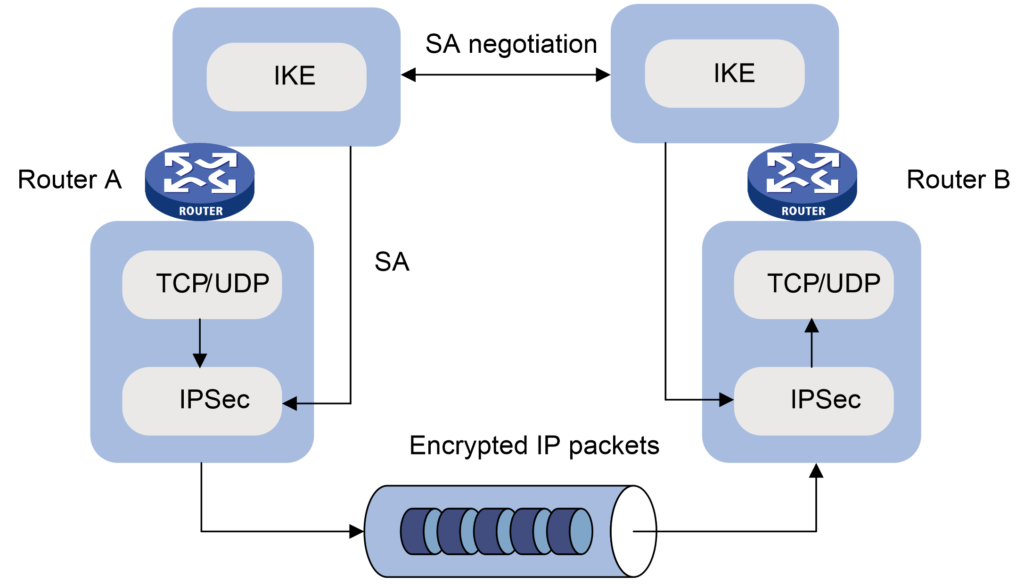
IKE plays an important role in negotiating security associations (SAs) for IP security (IPsec). SAs are security policies that define how two or more entities communicate with one another. When attempting to build a VPN tunnel or connection, both parties employ and represent a set of algorithms and mutually agreed-upon keys.
IKE standards are available in two versions:
RFC 2409 defines the IKE protocol, while RFC 7296 defines IKE version 2 (IKEv2).
How does IKE function in IPsec?
IKE is a component of IPsec, a set of protocols and methods intended to secure sensitive data sent across a network. The Internet Engineering Task Force (IETF) created IPsec to provide security by authenticating and encrypting IP network packets, as well as securing VPNs.
IKE defines an automatic way of negotiation and authentication for IPsec SAs in IPsec. Because it negotiates security, this is essential for the encryption and decryption processes. IKE provides various advantages for IPsec configuration, including automatic negotiation and authentication, anti-replay services, support for certification authorities, and the ability to change encryption keys during an IPsec connection.
The IKE protocol creates a SA using User Datagram Protocol (UDP) packets, which typically require four to six packets with two to three messages. An IPsec stack intercepts relevant IP packets, encrypting and decrypting them as needed
Understanding IKE’s Phases 1 and 2
IKE’s initial version establishes secure communication connections in two stages: phase 1 and phase 2.
In step 1, an authenticated connection is established between the host and the user using a preshared key or a digital certificate. The purpose is to safeguard communications during phase 2. The Diffie-Hellman key exchange technique establishes a secure communication channel for authentication. To generate decryption keys, this digital encryption approach uses numbers raised to particular powers. The outcome of the negotiation should be session keys and one bidirectional SA.
The first phase acts in one of two modes: main mode or aggressive mode. The primary mode entails both parties exchanging three two-way exchanges totaling six messages. The first two messages confirm the techniques for encryption and authentication. The second set of two messages initiates a Diffie-Hellman key exchange in which both sides supply a random integer. The final batch of communications confirms each party’s identity.
The aggressive mode does the same operation as the main mode, but in only two exchanges of three messages. The main mode encrypts both participants’ identities, whereas the aggressive mode does not.
Phase 2 of IKE negotiates a SA to encrypt data transmitted over IPsec utilizing the secure channel established in phase 1. As a result, there exist at least two unidirectional SAs. Both sides also share ideas on which security parameter to utilize in the SA.
Phase 2 has only one operating mode: fast mode. Quick mode gives you three options: proxy IDs, perfect forward secrecy (PFS), and replay protection. Each participant’s proxy ID is shared with the others. PFS provides keys that are independent of previous keys. Replay protection is a security mechanism used to prevent replay attacks.
The main and aggressive modes discovered in phase 1 are only applicable to IKE version 1, not IKE version 2.