Actionable strategies for secure access management in cloud environments. Learn how CISOs can enhance cloud security with MFA, RBAC, JIT access, and more.
Top 10 Data Loss Prevention (DLP) strategies for cloud-based systems to safeguard sensitive data, mitigate risks, and ensure regulatory compliance.
Top 10 cloud security misconfigurations and best practices for preventing vulnerabilities. Protect your cloud infrastructure from threats
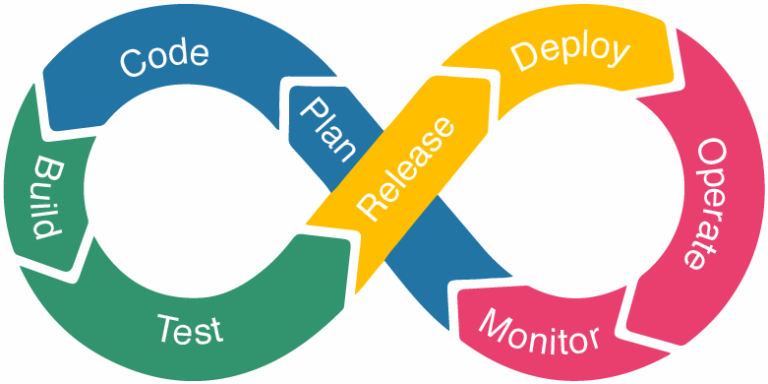
Build a secure DevOps pipeline with our DevSecOps guide. Discover best practices for embedding security at every stage of development
Businesses can protect against ransomware attacks with robust strategies like backups, endpoint protection, employee training, and incident response plans.
No posts found