Learn how to identify fake or scam websites by checking Trust Seals, reviewing content quality, verifying social media credentials, and more.
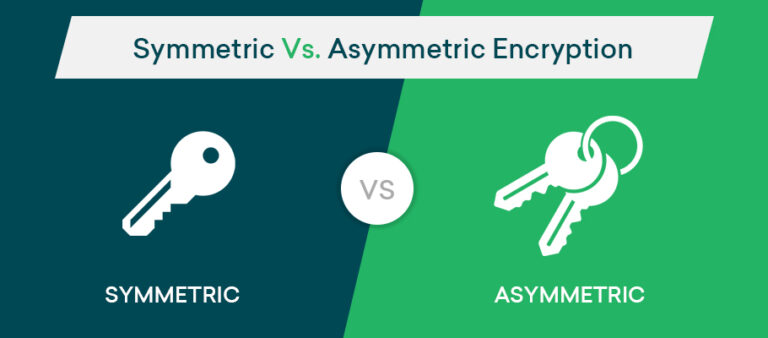
Explore the pros and cons of symmetric and asymmetric encryption to determine which provides stronger security for your sensitive data
Explore the differences between 128-bit and 256-bit encryption, including their security levels and performance in protecting sensitive data
Enable web security by installing trusted SSL certificates to protect user data, build trust, and improve your site's search rankings
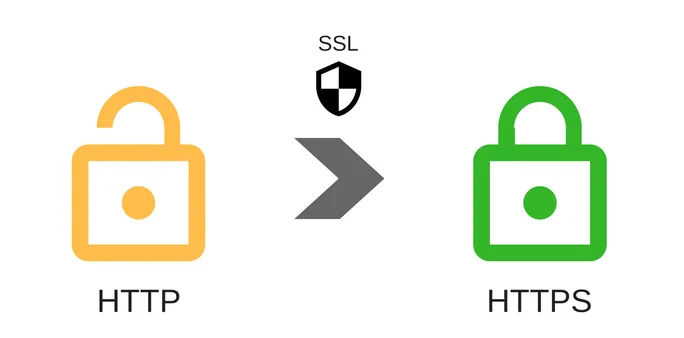
Understand the difference between HTTP and HTTPS, and how HTTPS offers enhanced security through encryption, protecting user data and improving website rankings.
No posts found